BSides Toronto 2025
Standing in front of a room full of security professionals at BSides Toronto, I had a moment of clarity: I had spent two months researching AI security, built a working conceptual dashboard demo, and prepared a 15-minute talk. But nothing really prepares you for that first moment when you look up and realize people are actually waiting to hear what you have to say.

This is the story of my first conference talk—what I learned, what I’d do differently, and why I’d encourage anyone on the fence about speaking to just submit that CFP.
When BSides Toronto accepted my proposal on “AI Agents: Your New Security Team Members or Biggest Threat?”, I had about 25 days to turn research notes and a working demo into an actual presentation.
The Preparation Process
I’d never given a conference talk before, so I treated preparation like a project. I structured the talk around five sections: the AI threat landscape, defense capabilities from research, a live dashboard demo, implementation reality, and open discussion. The key was balancing data with story—I didn’t want to just read statistics, I wanted to explain what they meant. The dashboard took the longest—I built a working HTML/CSS/JavaScript dashboard that visualized real-time threat detection, email analysis with confidence scoring, and the critical insight: AI handling 1000+ routine alerts while escalating 12 complex threats to humans. I wanted people to see what AI security operations actually look like, not just hear about it.
Creating the slides took several iterations. Early versions were too text-heavy—basically bullet points I was planning to read. I eventually stripped them down to visuals and key stats, using the slides as prompts rather than scripts. One decision I’m glad I made: I added a slide showing “Expectations vs. Reality” for AI deployment—clean dashboards versus alert chaos. It acknowledged the gap between vendor demos and actual implementation.
Practicing delivery is where I learned how different it is to rehearse alone versus present to people. I practiced the talk maybe 10-15 times in an empty room, timing myself obsessively since the talk needed to be 15 minutes to leave room for Q&A. I wrote detailed voice-over notes for each slide, but here’s what I learned: writing out exactly what to say word-for-word made me sound robotic. The best practice runs were when I knew my key points but let myself explain them naturally. What I worried about most? The demo. I tested it on three different laptops and brought a backup version on a USB drive. (Spoiler: it worked fine. But the backup plan helped me sleep the night before.)
The Day Of
BSides Toronto had a great energy—exactly the community-focused vibe I’d heard about. Walking in, I saw people already deep in technical conversations, trading war stories, and genuinely interested in learning from each other. My talk was scheduled for the afternoon, so I attended a few sessions in the morning, which helped me calibrate what BSides audiences respond to: authenticity over polish, practical insights over theory, and honest assessments over vendor pitches.
About 20 minutes before my slot, the nerves hit harder than I expected. Not panic, but that heightened awareness where you suddenly remember every possible thing that could go wrong. I did a quick tech check, confirmed the dashboard loaded, and took a few deep breaths.

Then I was on. The first 30 seconds felt surreal—looking out at a room of people who had chosen to spend their afternoon listening to me talk about AI security. But once I got through my opening (“With AI-powered attacks surging 67% in 2024, can we actually use AI to defend ourselves?”), muscle memory from all that practice kicked in.
About 45 seconds into the talk, I spotted my manager in the audience. Nobody told me he’d be there. There’s a special kind of adrenaline that kicks in when you realize the person who writes your performance reviews is watching you talk about AI security research you did “by night.” Suddenly every stat needed to be extra accurate, every claim needed to be perfectly defensible. The bar for “this better be good” just went up significantly. The dashboard demo was the moment I’d been most nervous about, but it ended up being the strongest part of the talk. When I showed the escalation queue—12 items requiring human judgment versus 1000+ auto-processed—I could see people leaning in. That visual of AI explaining “Novel attack pattern detected – requires human expertise” seemed to click with the audience.

What I Learned
This is the section I wish I’d read before my first talk, so I’m going to be specific about what worked, what didn’t, and what surprised me.
What Worked
Starting with concrete data grabbed attention immediately—opening with threat statistics (55% AI improvement, 67% of attacks using AI, 95% cost savings for attackers) made abstract threats concrete. The dashboard demo was particularly effective because visual demonstrations beat verbal descriptions every time; people could see what AI security operations look like rather than just imagining it. Being honest about limitations built credibility—saying upfront “This is research synthesis plus a conceptual demo, not a production case study” resonated with BSides audiences who respect honesty over overselling.
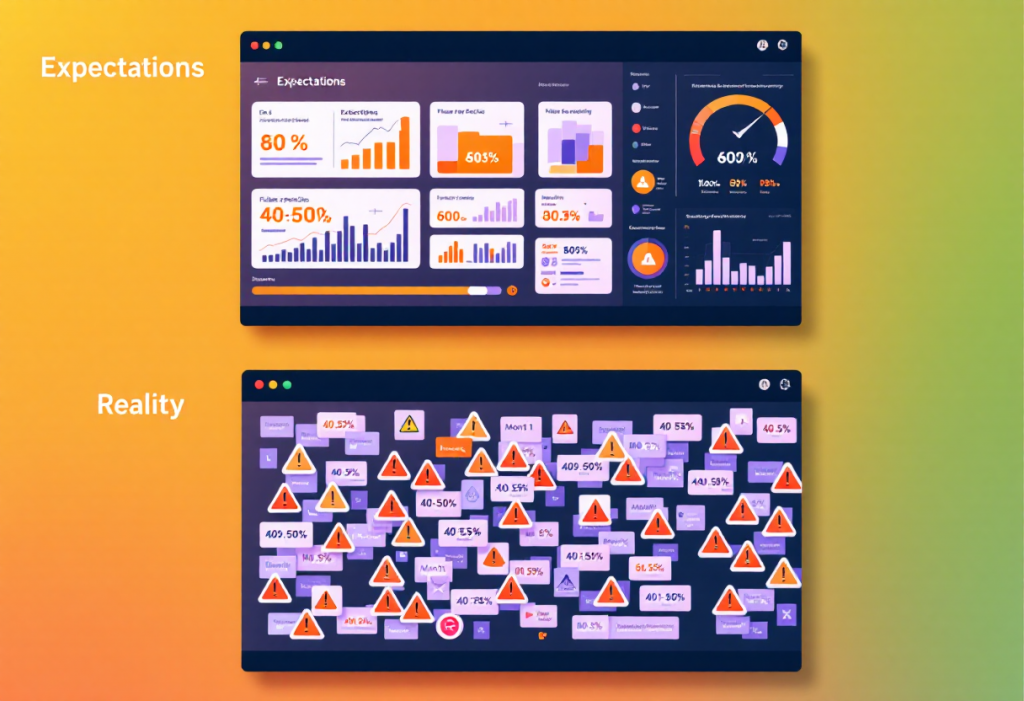
The “expectations vs. reality” slide showing the gap between clean vendor demos and messy real-world implementation (40-50% false positives in month one) got visible nods of recognition. Finally, positioning myself as a learner by ending with “I want to hear from you—what worked, what failed in your deployments?” turned it into a conversation rather than a lecture.
What I’d Change
Eye contact with the audience is the big one—I relied too heavily on my notes, which broke the connection with people in front of me. I was so focused on remembering what to say next that I spent too much time looking down instead of engaging. For next time, I need to know the arc of the talk well enough that my notes are just waypoints, not a script. I also rushed through the “How AI Detection Works” section because I was nervous about timing, but ironically finished with about 2 minutes to spare—I could have slowed down and let those technical concepts breathe more. Audience interaction was another miss: I asked one rhetorical question but didn’t pause for a show of hands or actual engagement. BSides crowds are participatory, and I should have built in 2-3 moments where I directly asked about their experiences. Finally, some of my section transitions were abrupt—the jump from “threat landscape” to “defense capabilities” needed a better bridge, something like “Now here’s the good news…” to signal the shift.
What Surprised Me
The nerves were manageable—I expected to be terrified, but it was more like heightened focus, and once I started talking, the preparation took over. BSides audiences actually want you to succeed: several people were taking notes, a few were nodding at key points, and that feedback helped me relax into the delivery. The Q&A was the best part—people asked thoughtful questions about false positive handling, integration with existing tools, and whether certain attack vectors could evade AI detection, which told me the content had landed and they were thinking critically about implementation. What surprised me most was that post-talk connections mattered more than the talk itself: within a few days, I had LinkedIn messages from a cybersecurity research doctor, a TASK.to organizer, and several practitioners dealing with similar challenges.
The Response
The Q&A revealed what resonated most. Someone asked about the 2-3 month tuning period—how to convince leadership to invest when month one shows 40-50% false positives. Another person wanted to know specific tools for getting started with AI security on a limited budget. These weren’t softball questions; they were from practitioners thinking about actual implementation.
Several people approached me afterward. One person mentioned they’re piloting AI security and hitting exactly the data quality challenges I’d described. Another asked for the GitHub link to the dashboard code. A third wanted to continue the conversation about whether AI could detect novel attack patterns or just known threats with variations.
The LinkedIn connections that followed were particularly interesting. A research doctor in cybersecurity reached out. The organizer of TASK.to connected on LinkedIn. People I’d never met were sending messages saying “great talk” or asking follow-up questions about specific research sources.
Within a week, the YouTube video of the talk was published. Watching myself present for the first time was… instructive. You see every mistake magnified, but you also see what the audience saw—which is usually less awkward than what you felt on stage.
What’s Next
I learned more from one 15-minute talk than from months of preparation, and I learned exactly what I need to improve. I’ve joined Toastmasters to work on the fundamentals: eye contact, pacing, vocal variety, and the ability to improvise when I lose my place. The technical content I can handle—I’m a practitioner with research to back it up—but delivery is a skill that requires deliberate practice. Would I speak again? Absolutely. Knowing what I know now, I’d probably submit to 2-3 conferences over the next year. The second talk is supposedly much easier because you’ve demystified the process—you know what stage nerves feel like, how to read audience engagement, and how to recover when you stumble.
If you’re on the fence about submitting a CFP to BSides or any conference: do it. You don’t need to be a world-class expert. You need to have learned something worth sharing and be willing to share it honestly. The BSides community, in particular, values practitioners sharing real experiences over polished corporate presentations. The gap between “I should speak about this someday” and actually submitting a proposal is smaller than you think. And the gap between submitting and actually giving the talk? That’s where all the growth happens.
For Future First-Time Speakers
If you’re considering your first technical talk, here’s what I’d tell you:
- Start with community-focused conferences like BSides. They want new voices, they’re supportive of first-timers, and the audience is there to learn, not judge.
- Submit even if you don’t feel “ready.” You’ll never feel ready. The act of preparing forces you to organize your knowledge in ways that make you more ready than you realized. Your talk doesn’t have to be groundbreaking—it just has to be useful.
- Practice your talk, but don’t memorize it. Know your key points cold, know your transitions, but let the explanation flow naturally rather than reciting memorized phrases.
- Have a backup plan for demos. If you’re showing live tech, test it on multiple systems, have screenshots as a backup, and know how you’ll proceed if it fails.
- The audience wants you to succeed—they’re rooting for you. One talk makes the next one 10x easier. The biggest barrier is the unknown. Once you’ve done one, you know what it feels like, and it becomes repeatable.
Resources & Links
- Watch the talk here: YouTube presentation link,
- Link to repo: GitHub repository
If you attended the talk or watched the replay, I’d love to hear what resonated or what questions you still have. And if you’re considering your first conference talk, feel free to reach out—I’m happy to share more about the process.
This was my first conference talk. The next one will be better because I’ve done one. That’s how this works. If you’ve been thinking about speaking but haven’t taken the leap, consider this your encouragement: submit that CFP. The community needs your perspective.
